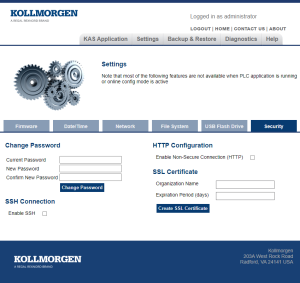
Security tab
-
This tab is only visible for PCMM2G controllers.
This tab is used to:
- Change the user's Web server account password.
See Change the User's Web server Account Password. - Manage remote access to the controller via SSH.
See SSH Connection. - Manage non-secure connection access via HTTP.
See HTTP / HTTPS Configuration. - View the current SSL certificate’s details.
See SSL Certificate Details. - Create SSL certificates for HTTPS connections.
See Create SSL Certificate.
Figure 1: Security tab
Change the Password
This area is used to Change the User's Web server Account Password.
SSH Connection
This area is used to manage the Remote Access to the PCMM2G controller via SSH (Secure Shell).
- SSH is a network protocol that gives the users a secure way to access an external system remotely.
- It provides a text-based interface by spawning a remote shell.
- By default, the
SSH access is disabled on the PCMM2G to enhance security.
- By keeping SSH access off, the PCMM2G controller minimizes the risk of external attacks.
- SSH may need to be enabled in certain advanced troubleshooting scenarios.
- SSH access allows diagnostic commands and access to system logs.
- See Using SSH.
HTTP / HTTPS Configuration
This area is used to manage the non-secure connection to the PCMM2G using the HTTP (Hypertext Transfer Protocol).
- HTTP is a communication protocol that transfers unencrypted data between the user’s browser and the webserver.
- HTTPS is a secure extension of HTTP that provides encrypting and verification to the data transferred between the user’s browser and the webserver.
- By default, HTTP connections are disabled and will redirect to HTTPS on the PCMM2G to enhance security.
- By keeping HTTP disabled, the PCMM2G minimizes the risk of vulnerable data being exposed.
- HTTP may need to be enabled in certain legacy configurations that do not support HTTPS.
SSL Certificate Details
This area is used to view the status of the certificate and its expiration date.
The certificate statuses are:
- Installed
- Not Installed
- Invalid - IP Address Mismatch
- Invalid - Expired
Create SSL Certificate
This area is used to create an SSL (Secure Sockets Layer) certificate on the PCMM2G.
- SSL certificates are used to enable HTTPS connections on the PCMM2G.
- When creating an SSL certificate, the PCMM2G’s current IP address is linked to the certificate with an expiration date.
- The certificate is valid only when the IP address listed on the certificate is identical to the PCMM2G’s IP address.
- It is recommended to set a static IP address for the PCMM2G when using an SSL certificate.
- To ensure secure and trusted communications with the Web server through HTTPS, the SSL certificate must be installed on the user’s machine after creating it.
Important Notes
Security
To maintain the security of the device, always disable SSH access and HTTP connections when they are no longer needed.
Access Control
Ensure that only authorized personnel have access to the web interface and change security settings.
SFTP Support
File transfer using SFTP (Secure File Transfer Protocol) is not supported when SSH is disabled.
SFTP relies on SSH for secure file transfer, so you will need to enable SSH to use SFTP.
|
Setting |
Description |
|---|---|
|
Enable SSH |
Changing the state of the check box immediately changes the configuration on the controller.
|
|
Enable Non-Secure Connection (HTTP) |
Changing the state of the check box changes the HTTP configuration on the controller and reboots the controller.
|